Every year, phishing attacks become more widespread and dangerous. According to the FBI, phishing was the most common cyberattack in 2020, and 241,324 phishing incidents were reported in that same year — that's more than double the 114,702 incidents reported in 2019! What’s even worse is cybercriminals are taking advantage of the COVID-19 pandemic to find new phishing victims.
So how well can your business prevent today’s phishing scams? Take our short quiz to find out. Each question will test your business’s security awareness. At the end of the quiz, you should be more knowledgeable about dealing with phishing scams in the future.
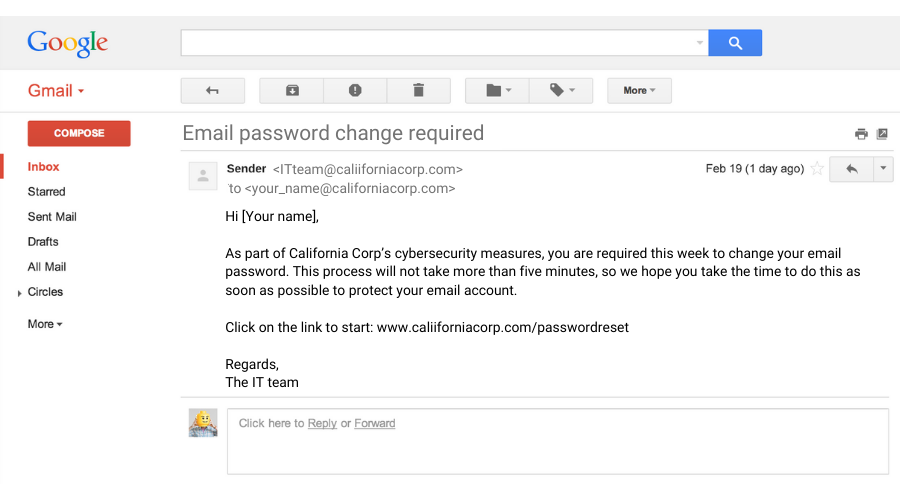
1. Is the email below a phishing scam or a legitimate message?
A. Phishing scam
B. Legitimate message
Correct answer: A. Phishing scam
There are two signs of a phishing scam in this email. First, the sender’s email address is designed to look like the recipient’s email address. Second, the link provided in the email body also imitates the business’s domain. Clicking on the link will take you to a fraudulent website that will ask for your login credentials. If you give them out, the attackers will gain access to your account, enabling them to steal sensitive information.
Be careful when dealing with suspicious messages like this. Before interacting with them, make sure to verify the sender's links by hovering over them to see their true location.
2. You are the head of your company’s finance department. Is the email below a phishing scam or a legitimate message?
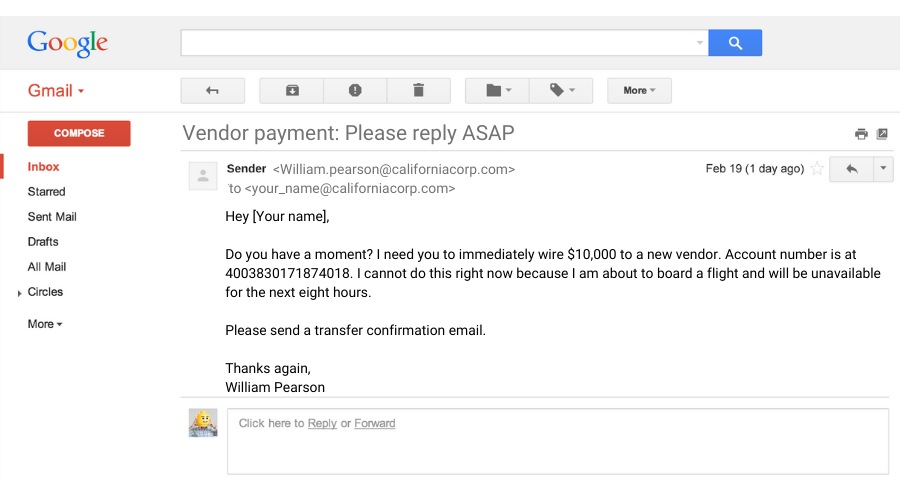
A. Phishing scam
B. Legitimate message
Correct answer: A. Phishing scam
The email above is a classic example of an email used in business email compromise (BEC) attacks. BEC is a type of phishing scam designed to trick recipients into making unauthorized wire transfer payments. Cybercriminals also use BEC to infiltrates or imitate official business accounts to conduct fraudulent transactions
In the example above, the attacker was able to gain access to one of your company’s email accounts to request a payment. Since the message came from a legitimate address, you might not recognize it as a scam, so you’re more likely to comply with the request. BEC attacks can also bypass spam filters and antivirus software.
To avoid falling victim to BEC attacks, always confirm requests for sensitive transactions like wire transfers. You can do this by physically approaching or calling the person supposedly making the request. Employees should also enable multifactor authentication (MFA). With MFA, your workers need to present another set of login credentials in addition to passwords like a one-time passcode or a security key generated by a mobile authenticator app to confirm their identity. So even if an attacker steals an employee’s passwords, they won’t be able to break in without access to the other login credentials.
3. Below is an example of a phishing email. Aside from the fraudulent sender address, what are the other signs?
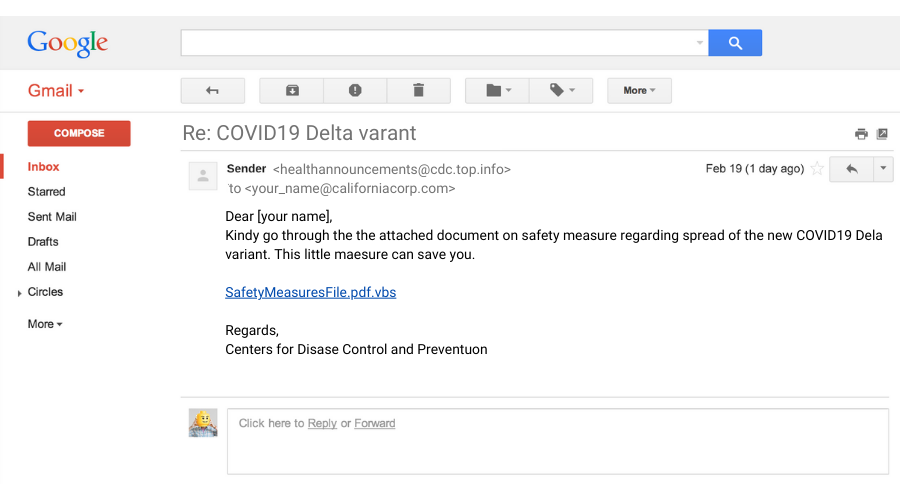
A. Grammatical and spelling errors
B. Attachment
C. Both
Correct answer: C. Both
The email above contains multiple grammatical and spelling errors. What’s more, the attachment is a script file disguised as a PDF file. Opening it could infect your computer with malware such as spyware and keyloggers that can steal sensitive information.
Make sure to inspect the contents of suspicious emails thoroughly. Under no circumstances will a professional company ask for confidential information via email or include attachments you weren't expecting.
Related article: Most commonly used phishing subject lines
4. You receive a text message purporting to be from Costco saying you won $5,000. To claim the prize, you need to reply with your bank information. What do you do?
A. Ask for more information about the prize
B. Reply with your bank information
C. Report it as a scam
Correct answer: C. Report it as a scam
As more people use their mobile phones as a productivity tool, cybercriminals are creating text-based scams called SMS phishing or smishing. Smishing involves attackers mass sending a text message claiming that the recipient has won a prize or their bank account has been locked. The recipient is then asked to click on a suspicious link or reply with their personal information.
Stay vigilant about these types of messages. Remember that reputable companies will never contact you directly to request personal or financial information. If you didn’t join any contest or know that your bank accounts have not been infiltrated, do not reply to the messages and report them to the Federal Trade Commission.
Smishing involves attackers mass sending a text message claiming that the recipient has won a prize or their bank account has been locked.
5. You receive a call from someone claiming to be from the IRS saying that you owe them money and must pay immediately. They also threaten your arrest if you don’t comply. What do you do?
A. Comply with their request
B. Ignore the request and hang up
C. Ask for more information
Correct answer: B. Ignore the request and hang up
This scheme is known as voice phishing or vishing, which involves cybercriminals making phone calls purporting to be from legitimate companies or government agencies to steal sensitive information.
In the example above, if you provide your banking information, the attacker will be able to make fraudulent purchases under your name or sell the data on the dark web.
Make it a habit to verify the authenticity of phone calls first and be suspicious of callers that request your login credentials to mitigate the risk of falling victim to vishing attacks. Remember that government agencies will never call you to demand immediate payment or ask for your banking information.
How did you do?
4–5 correct answers: Great job! You know how to deal with phishing attacks.
2–3 correct answers: Good, but there’s more to learn when it comes to preventing phishing attacks.
0–1 correct answer: You may need to brush up on your phishing knowledge.
When it comes to protecting businesses in California against phishing attacks and other cyberattacks, nobody does it better than Complete Document Solutions. We will provide you with powerful solutions to ensure your data’s security, and detect and repel harmful programs in real time. Request a FREE IT assessment today.